Edit tailnet policy file
You can edit your tailnet policy file by using the Access Controls page of the admin console, GitOps for Tailscale ACLs, or the Tailscale API. Refer to ACL syntax.
You need to be an Owner, Admin, or Network admin to edit the tailnet policy file.
Previewing changes
When editing the tailnet policy file in the Access Controls page of the admin console, you can preview the permissions granted to your users.
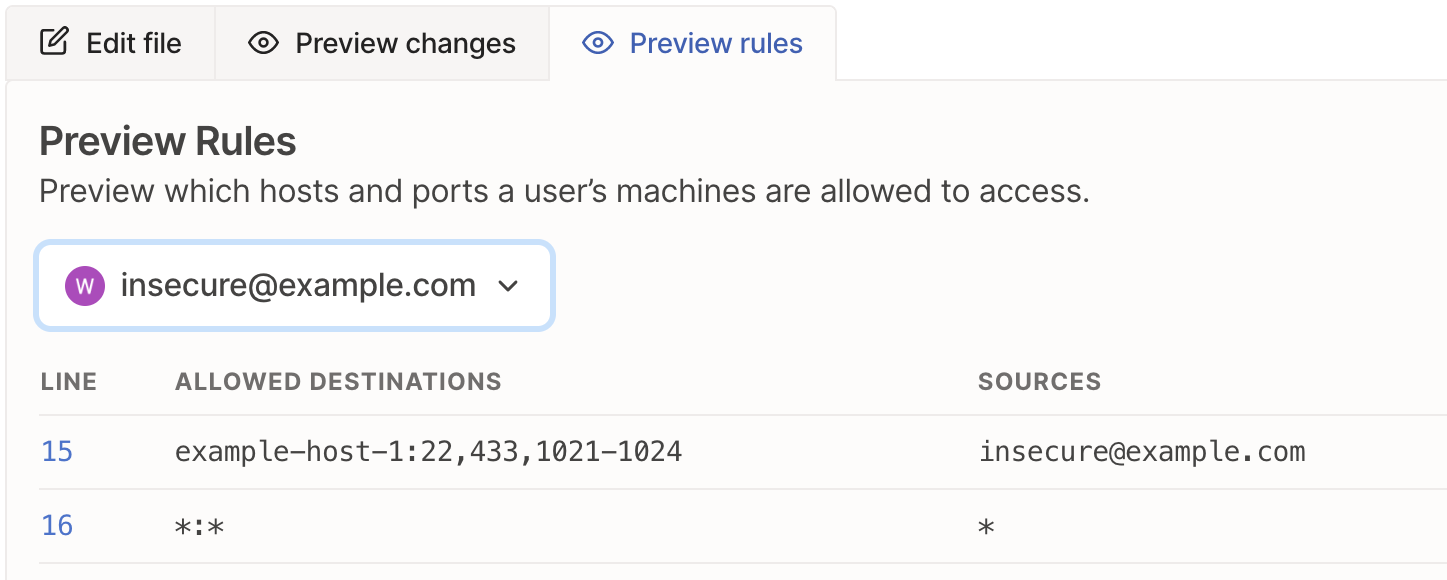
To do so, open the Preview rules tab and select a user from the dropdown. A list of destinations (one per line) accessible to the specified user is shown, as well the line number that defines that rule. It also includes any other users/groups that can access that destination due to that rule.
Another way to increase confidence in your changes is to define some ACL tests, to check that your changes don't accidentally remove access to an important system, or accidentally open up access wider than you intended.
Debugging ACLs
To debug whether ACLs block communication between nodes, use tailscale ping.
There are two types of ping checks that tailscale ping can do: TSMP and ICMP.
TSMP pings check whether two nodes can establish a network connection, but
stops before the ACL check. Use tailscale ping --tsmp to send a TSMP ping.
ICMP pings check the end-to-end connectivity between nodes, including ACLs.
Use tailscale ping --icmp or regular ping to send an ICMP ping.
If TSMP ping succeeds but ICMP ping fails, connections between nodes are likely blocked by ACLs. If TSMP ping fails, nodes cannot establish a network connection, even though ACLs may allow connections. If both TSMP and ICMP pings succeed but connections still fail, check the port numbers in your ACLs and services you are trying to connect to.
In addition to manual testing, built-in ACL tests ensure that specific connections are allowed and prevent ACL changes from accidentally breaking these connections.
Reverting changes
You can revert your tailnet policy file from a previous date and time, in the Configuration logs page of the admin console. For instruction, see Reverting ACLs from audit logs.
This option is not available if you are using GitOps for Tailscale ACLs.