Secure a Windows RDP (Remote Desktop Protocol) server
Remote Desktop Protocol (also known as Windows Remote Desktop or Windows Terminal Server) is among the most commonly exploited targets for ransomware and other attackers.
One way to vastly reduce your attack surface is to avoid exposing your RDP on the Internet at all.
With Tailscale, you can allow only authorized clients on your Tailscale network to connect to your RDP servers, without opening any firewall ports.
Tailscale works transparently to the RDP client, securing your network without making RDP any harder to use.
Prerequisites
This guide requires you to be on a Windows system that can serve as a Remote Desktop Server. The guide was written using a Windows 10 Pro machine, but this process should work on modern Windows Server releases as well.
You’ll also need a Tailscale network, known as a tailnet. For information about creating a tailnet, see the Tailscale quickstart.
Step 1: Open Windows Firewall with Advanced Security
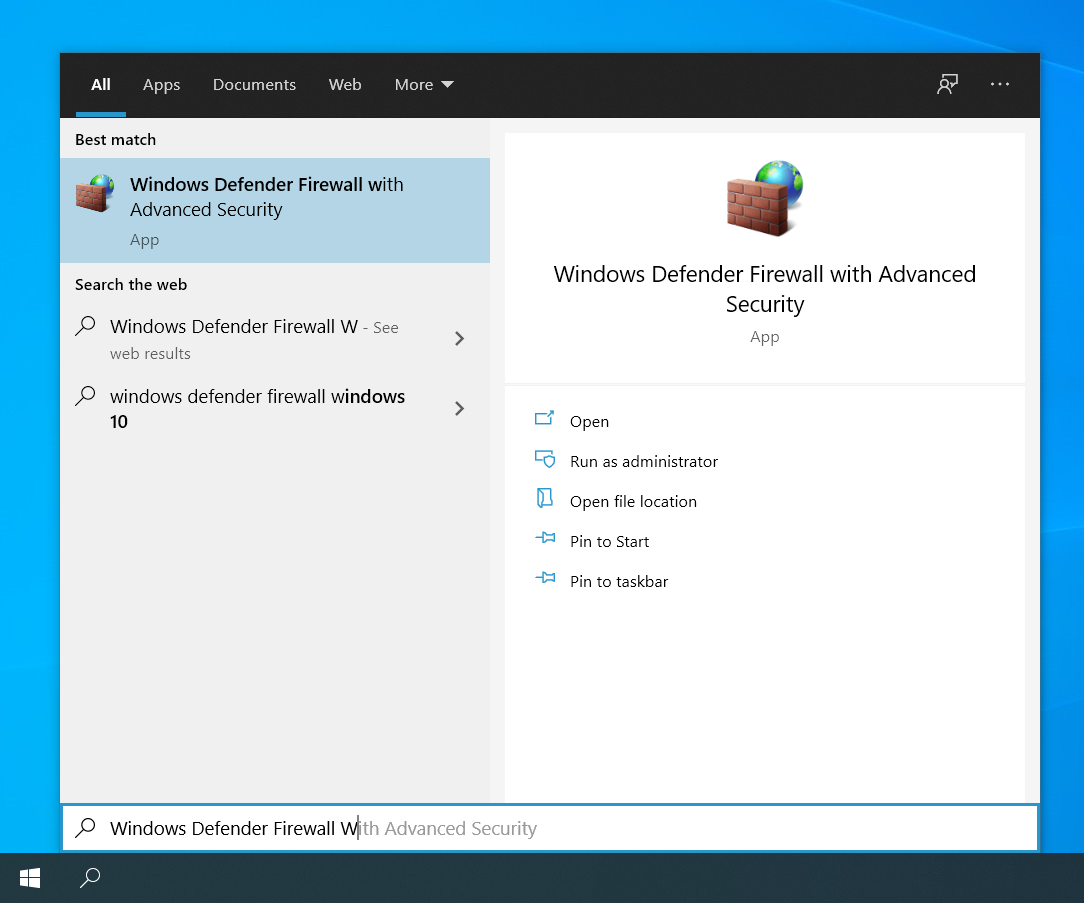
Open your Start Menu, type Windows Defender Firewall with Advanced Security, and click its icon to open the Advanced Security console of the Windows Firewall.
Step 2: Find remote desktop rules
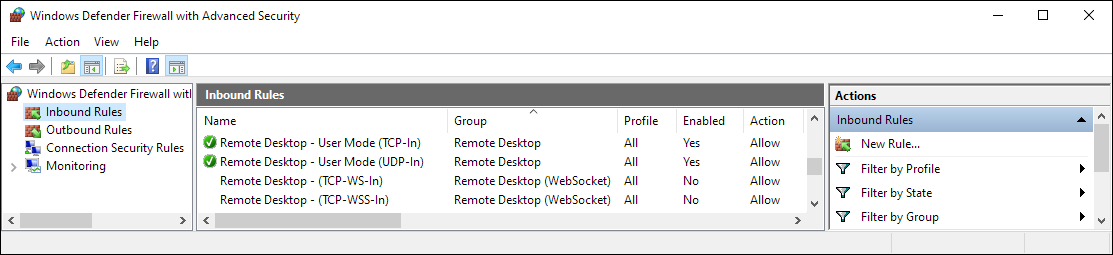
On the left-hand side pane of the Windows Defender Firewall window, click Advanced settings and then click Inbound Rules. The list of inbound firewall rules should appear in the central pane. Scroll down to the rules for Remote Desktop — User Mode.
Step 3: Restrict access to Tailscale
Right-click the TCP rule, and click Properties. In the Properties window, select the Scope tab on the top.
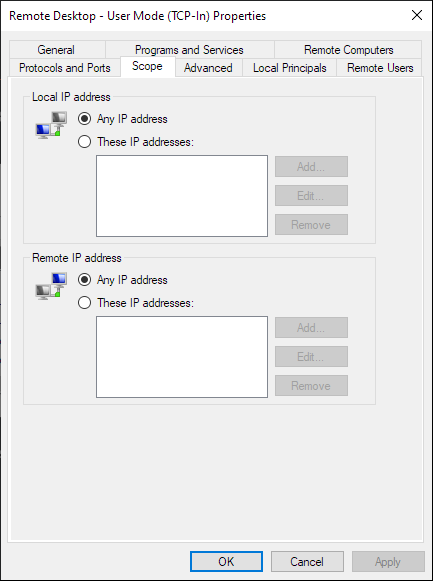
Under Remote IP Addresses, choose These IP addresses: and then click the Add button to add a range of allowed IPs. Since Tailscale allocates IP addresses in the 100.64.0.0/10 subnet, and we want to allow access to Tailscale IP addresses, type in that range and click OK.

Click OK in the Properties window to confirm your changes.
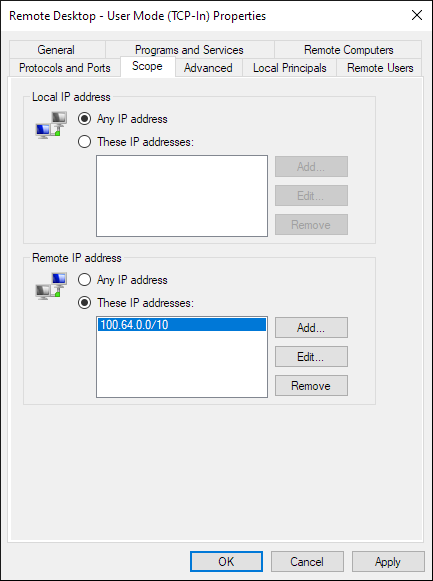
Finally, repeat the steps above for the UDP rule as well.
And we’re done! Verify that another computer on your Tailscale network can connect to Remote Desktop, and that a computer accessing from another IP (for example, a 10.x.x.x or 192.168.x.x address on your network) cannot. At this point, any node on your Tailscale network should be able to access Remote Desktop from the server. To control access within your Tailscale network, you should use Access Control Lists (ACLs).